The proliferation of Internet of Things (IoT) ecosystems has introduced unprecedented levels of connectivity across industrial, commercial, and domestic environments. However, IoT deployments often suffer from constrained computing resources, limited embedded security controls, weak firmware baselines, and heterogeneous communication standards. These characteristics significantly increase the attack surface, allowing adversaries to execute Advanced Persistent Threats (APTs), lateral movement, supply-chain compromises, and data-exfiltration attacks.
To address these challenges, the proposed architecture (illustrated above) integrates open-source security platforms, predictive threat intelligence, and automated machine learning (ML/AI) to establish an adaptive, scalable, and cost-efficient IoT security framework.
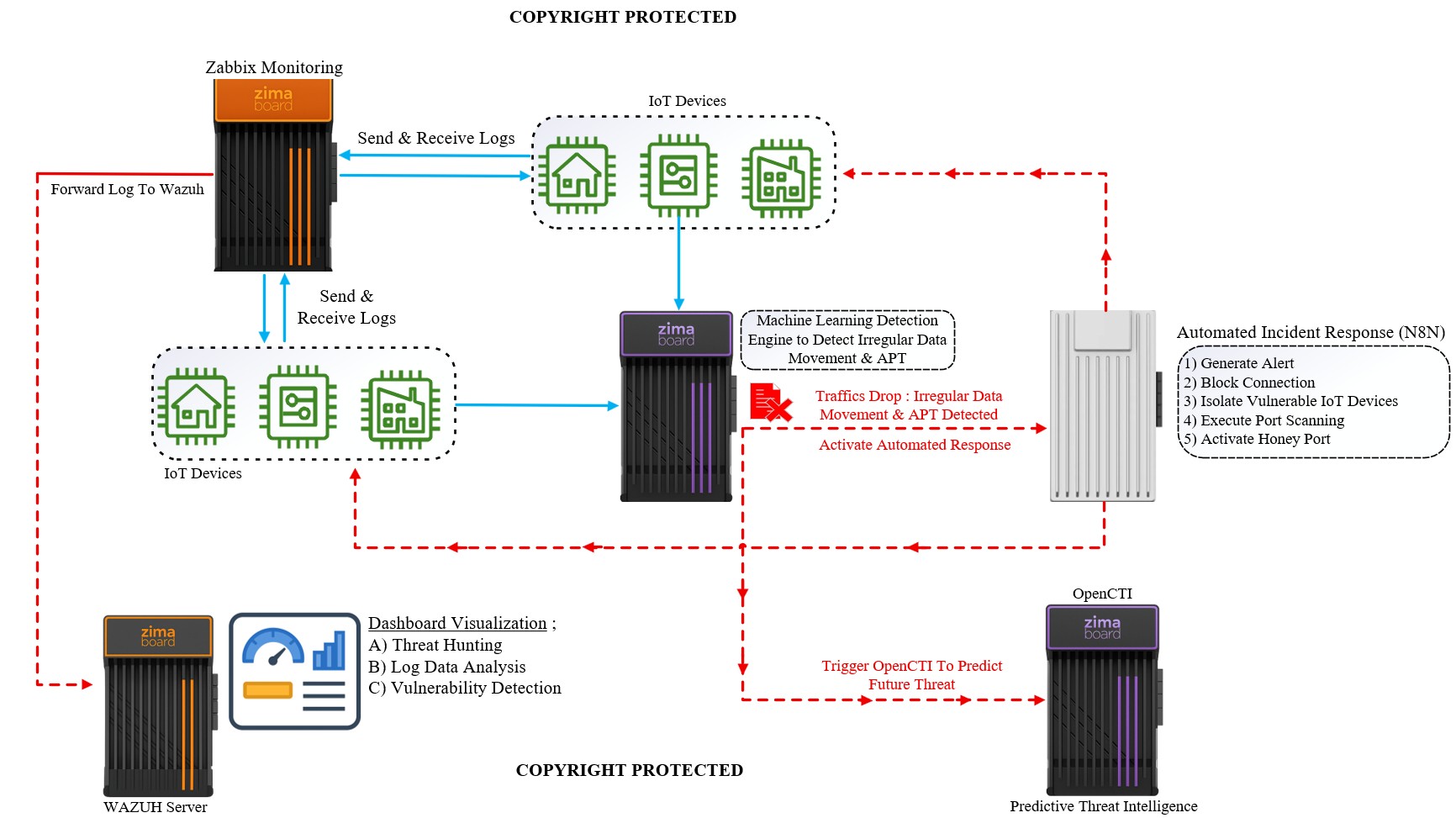
Key Benefits of the Proposed Open-Source and Automated ML/AI IoT Security Design
The integration of Zabbix, Wazuh, Machine Learning Detection Engine, N8N Automated Response, and OpenCTI Threat Intelligence offers significant operational, economic, and security advantages for large-scale IoT ecosystems. The main benefits are as follows:
1. Enhanced Threat Detection and Prevention
The design enables real-time, behavior-based detection of attacks, including irregular data movement, botnet behavior, and APT activities. Machine learning models continuously analyze network telemetry and learn evolving threat patterns, improving detection accuracy compared to static signature-based systems.
2. Automated Incident Response and Lower Response Time
With N8N automation, the system can autonomously:
- Block malicious traffic or isolate compromised IoT devices
- Execute targeted network scans
- Activate deception environments (e.g., honey ports)
- Generate alerts to SOC analysts
This minimizes the time between threat detection and containment.
3. Predictive Threat Intelligence Capability
Using OpenCTI, attack patterns are not only detected but also correlated with external threat feeds. The system:
- Identifies adversary TTPs early (aligned with MITRE ATT&CK)
- Supports predictive modeling for future attacks
- Enhances security decision-making and adaptive policy tuning
4. Reduced Man-Hours and Operational Workload
Automation significantly decreases manual SOC intervention, reducing analyst fatigue and improving retention. Dashboards consolidate threat hunting, vulnerability insights, and log analytics.
The proposed design delivers a comprehensive, cost-effective, and adaptive security architecture for IoT ecosystems by combining open-source platforms, edge-based ML detection, automated SOAR workflows, and predictive threat intelligence. This framework enhances resilience, reduces operational burden, and ensures sustainable and scalable IoT security management.
